As organizations increasingly migrate their workloads to the cloud, securing access to critical applications and resources becomes paramount. Traditionally, Virtual Private Networks (VPNs) have been the go-to solution for secure remote access. However, as cloud environments and remote workforces grow, limitations in traditional VPNs have become more apparent.
 AWS Verified Access, a cloud-native solution designed to offer secure, scalable, and identity-based access without the overhead and complexity of traditional VPNs. In this post, we’ll compare AWS Verified Access with traditional VPNs to help you determine which approach is best suited for your AWS environment.
AWS Verified Access, a cloud-native solution designed to offer secure, scalable, and identity-based access without the overhead and complexity of traditional VPNs. In this post, we’ll compare AWS Verified Access with traditional VPNs to help you determine which approach is best suited for your AWS environment.
Understanding the Basics
What is AWS Verified Access?
AWS Verified Access is a Zero Trust Network Access (ZTNA) solution that provides secure access to applications and services hosted in AWS. Unlike traditional VPNs, which grant network-level access, Verified Access focuses on application-level security. It evaluates each access request based on user identity, device posture, and other contextual factors, enforcing granular access control without requiring users to connect to a corporate network.
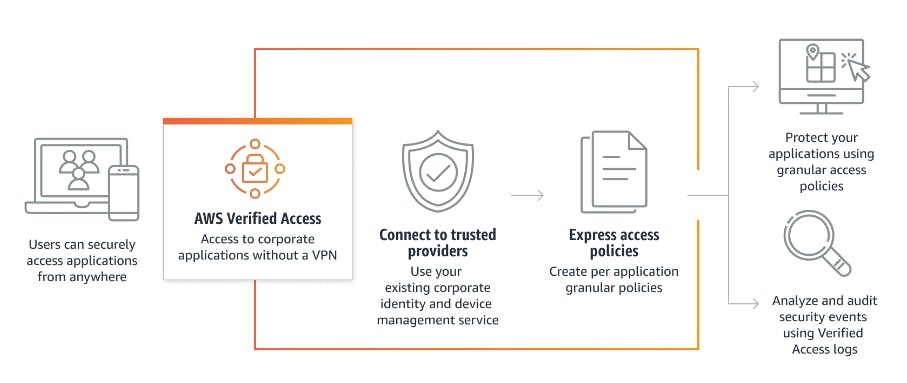 Key Features of AWS Verified Access:
Key Features of AWS Verified Access:
- Identity-Based Access: Integrates with AWS IAM Identity Center and other identity providers.
- Contextual Access Decisions: Access is granted based on identity, device, location, and other factors.
- No VPN Required: Direct, secure access to AWS applications without the need for a VPN tunnel.
- Granular Policy Control: Policies can be tailored to specific users, roles, and devices.
- Seamless AWS Integration: Native integration with AWS services like VPC, IAM, and CloudTrail.
What is a Traditional VPN?
A Virtual Private Network (VPN) creates a secure, encrypted connection between a user’s device and a corporate network. VPNs have been widely used to provide remote access to internal resources, allowing users to work securely from outside the office. However, VPNs operate at the network level, granting users broad access to the network once they are connected.
Key Features of Traditional VPNs:
- Network-Level Access: Users gain access to the entire network, not just specific applications.
- Encryption: Data is encrypted between the user’s device and the corporate network.
- Device-Agnostic: Works across various devices and operating systems.
- Broad Compatibility: Supports access to both on-premises and cloud-based resources.
- Established Technology: Widely understood and implemented across industries.
Few Popular Traditional VPNs
Before diving into the comparison, let’s briefly look at some of the most popular traditional VPN solutions used by organizations:
- Cisco AnyConnect: A widely used VPN solution that provides secure access to enterprise networks and applications. Cisco AnyConnect is known for its robust security features and compatibility with a range of devices and operating systems.
- Palo Alto Networks GlobalProtect: This VPN solution extends the security capabilities of Palo Alto Networks firewalls to remote users, offering comprehensive protection and integration with the company’s broader security suite.
- OpenVPN: An open-source VPN solution that is highly customizable and widely adopted across various industries. It supports a range of encryption standards and is often used by small to medium-sized businesses.
- Fortinet FortiClient: Part of Fortinet’s Security Fabric, FortiClient offers VPN capabilities along with endpoint security features, providing a comprehensive solution for secure remote access.
- Pulse Secure: A VPN solution that focuses on providing secure access to corporate networks and cloud applications. It is particularly popular in industries requiring high levels of security, such as finance and healthcare.
Comparing AWS Verified Access and Traditional VPNs
- Security Model
- AWS Verified Access: Follows a Zero Trust security model, where no user or device is trusted by default. Access is granted on a per-application basis, with decisions based on user identity, device posture, and other contextual factors. This minimizes the risk of lateral movement within the network if credentials are compromised.
- Traditional VPNs: Once connected, users typically have broad access to the network, increasing the risk of unauthorized access or lateral movement. VPNs do not natively support the Zero Trust model and require additional layers of security to achieve similar levels of control.
- Access Control
- AWS Verified Access: Provides fine-grained, identity-based access control at the application level. Policies can be defined to restrict access based on user roles, device compliance, location, and other contextual elements.
- Traditional VPNs: Primarily offer network-level access, with more limited capabilities for granular access control. Access is often all-or-nothing, with users gaining broad network access once authenticated.
- User Experience
- AWS Verified Access: Offers a seamless user experience without the need for a VPN client. Users can access applications directly through a browser or app, with access decisions made transparently in the background.
- Traditional VPNs: Requires users to install and configure VPN clients. Connecting to the VPN can be cumbersome, particularly for non-technical users, and may introduce latency in accessing resources.
- Scalability and Performance
- AWS Verified Access: Designed to scale with your AWS environment, making it easy to manage and secure access to applications as your organization grows. It eliminates the performance bottlenecks often associated with VPNs, as there’s no need to route traffic through a central VPN gateway.
- Traditional VPNs: VPN gateways can become performance bottlenecks, especially as the number of remote users increases. Scaling a VPN solution often requires significant investment in infrastructure and management overhead.
- Integration with AWS Services
- AWS Verified Access: Seamlessly integrates with AWS services like IAM, CloudTrail, and VPC. This native integration simplifies policy management, auditing, and monitoring, making it easier to maintain a secure environment.
- Traditional VPNs: While VPNs can be configured to provide access to AWS resources, they do not offer the same level of seamless integration. Managing and securing VPN connections in a cloud environment can be more complex and time-consuming.
Use Cases: When to Choose AWS Verified Access vs. Traditional VPNs
AWS Verified Access is Best For:
- Cloud-First Organizations: Companies that have a significant portion of their infrastructure in AWS and want to implement a Zero Trust security model.
- Application-Specific Access: Scenarios where users need secure access to specific applications without network-level access.
- Scalable Remote Work: Businesses with a large remote workforce that require a scalable, low-latency solution for secure application access.
Traditional VPNs are Best For:
- Hybrid Environments: Organizations that need to provide access to both on-premises and cloud resources.
- Legacy Systems: Environments where traditional applications require network-level access that a VPN can provide.
- Broad Network Access: Situations where users need full access to the corporate network, such as IT administrators or engineers.
Summary
While traditional VPNs have been a reliable solution for remote access, the rise of cloud-native applications and the Zero Trust security model have exposed their limitations. AWS Verified Access offers a modern, scalable, and secure alternative, particularly for organizations heavily invested in the AWS ecosystem. By providing identity-based, application-specific access, Verified Access reduces the attack surface and enhances security without compromising user experience.
For organizations looking to secure access to AWS resources while adopting a Zero Trust approach, AWS Verified Access is a clear choice. However, traditional VPNs may still be relevant for hybrid environments or specific use cases where network-level access is necessary. Ultimately, the best solution depends on your organization’s specific needs, infrastructure, and security requirements.




