About the customer
Drivers4Me is a driver aggregator startup, providing on-demand, mobile app based car driver hiring services. We provide experienced drivers in whole India. Our purpose is twofold; assist car owners find licensed individuals nearby, willing to provide them punctual, hassle-free, cost effective service, and help professional drivers or licensed individuals (companions) willing to provide services to potential customers on an hourly basis with transparency in price breakdown, encouraging drivers and customers alike to connect to one another using our mobile app.
Customer Challenge
Scalability Constraints:
The monolithic architecture hindered independent scaling of components, causing significant inefficiencies during peak loads. This resulted in difficulty accommodating increased user traffic, directly impacting business operations and customer experience. During high demand periods, the lack of scalability led to service slowdowns and unavailability, adversely affecting user satisfaction and business revenue.
Migration Complexity:
Transitioning from PythonAnywhere to AWS Cloud entails several technical challenges, including infrastructure setup, application deployment, and configuration. The complexity of this migration process posed risks to operational continuity and required careful planning to avoid extended downtime and data integrity issues.
Performance Issues:
The monolithic design caused performance bottlenecks, as all components were tightly coupled, leading to resource contention and inefficiency. This resulted in slow response times and degraded performance, especially during peak usage periods, negatively impacting user experience and business productivity.
Manual Deployment and Downtime:
The absence of automated deployment processes meant that deployments were manual, error-prone, and time-consuming. This led to frequent downtime during deployment windows, further disrupting business operations and reducing system reliability. The lack of CI/CD pipelines prevented regular releases and quick updates, limiting the ability to deliver new features and improvements promptly.
Security Requirements:
The customer demands a highly secure platform to safeguard sensitive data and ensure compliance with regulatory standards. Meeting these stringent security requirements is essential to maintain trust and avoid legal repercussions.
Workmates Core2Cloud Solution Approach
- We had analyzed the client’s application logic modules suitable for microservices.
- Module had isolated as a microservice with well-defined boundaries and responsibilities and communication between microservices had been organized, such as RESTful APIs, message queues, or other mechanisms.
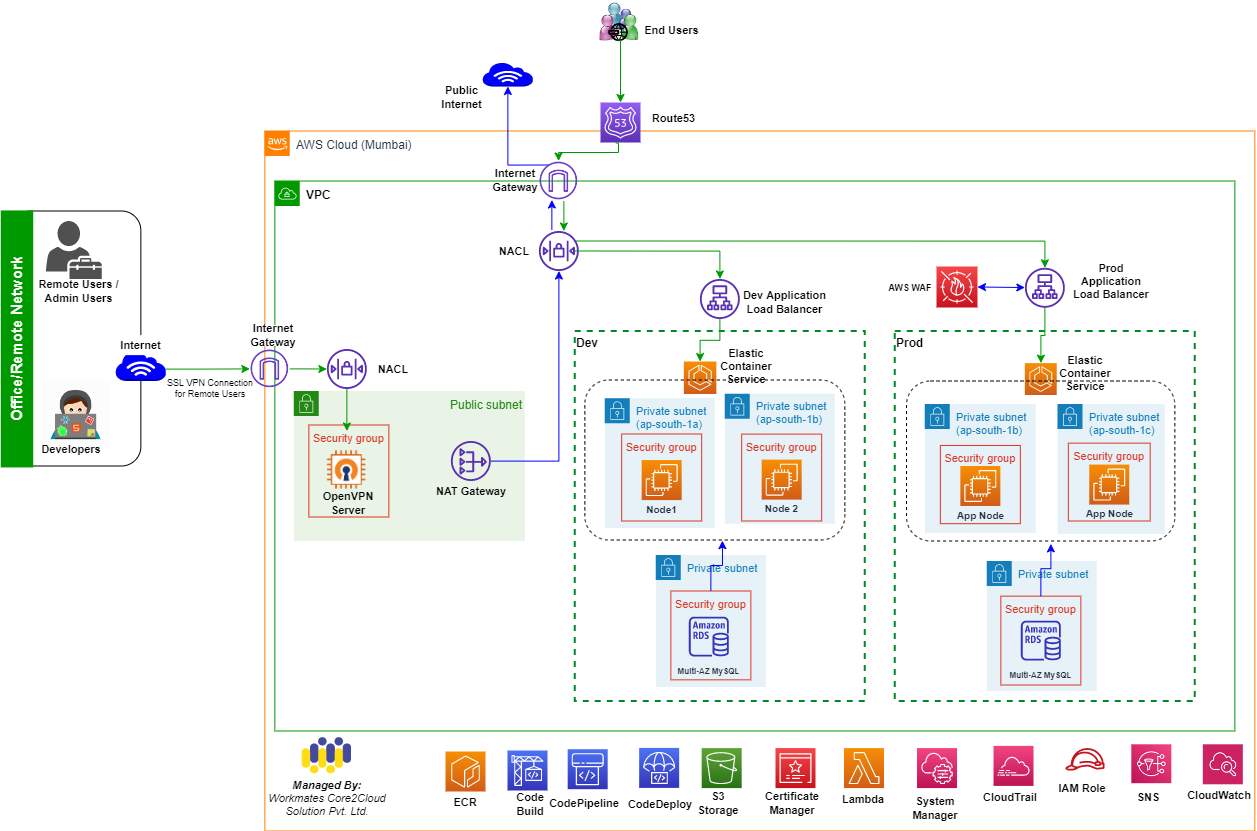
- To enable secure access, an SSL VPN was configured on the public network, allowing administrative users to access the clusters via this SSL VPN tunnel.
- The architecture was designed using microservices, and AWS Elastic Container Service (ECS) was employed to manage web applications and APIs.
- Infrastructure provisioning was automated on the AWS cloud using AWS CloudFormation.
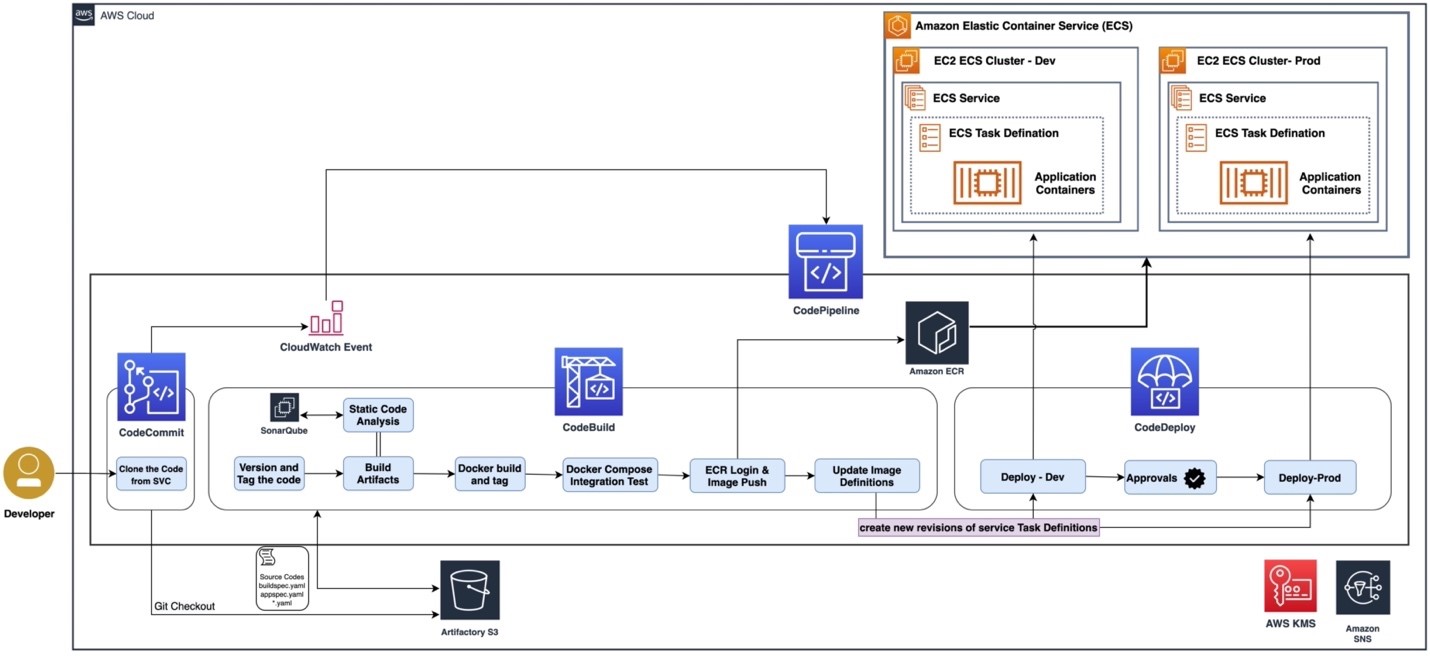
- A comprehensive Continuous Integration/Continuous Deployment (CI/CD) pipeline was implemented using AWS Code Pipeline.
- AWS CloudFormation templates were leveraged to automate the deployment of the entire architecture.
- We collaborated with the customer’s team to prepare non-root Docker containers, aligning with the microservices approach.
- Docker containers were stored in Amazon Elastic Container Registry (ECR), and access to the registry was managed via IAM roles.
- To ensure high availability and efficient traffic management, an AWS Application Load Balancer was configured for each workload.
- For the production phase, MYSQL databases were deployed on Amazon Elastic Compute Cloud (EC2) instances as a standalone cluster.
- AWS CloudWatch was enabled for infrastructure and application monitoring, facilitating robust microservices monitoring.
- Infrastructure and database backups were stored on Amazon S3 with a 15-day retention policy, providing accessible backup data at any time.
- AWS Config was implemented for continuous monitoring, assessment, and change management of AWS resource configurations.
- Systems Manager Patch Manager was configured to scan EC2 instances, assess compliance, and schedule patch installations.
- Parameter Store (Systems Manager) was utilized to securely store secrets and credentials. These secrets were securely accessed during the deployment stage of the CI/CD pipeline.
Results and Benefits
- Streamlined Deployment: Microservices on AWS ECS facilitated consistent and efficient deployments, reducing downtime, and enhancing user experience.
- Automated CI/CD: Implementation of automated CI/CD pipelines enabled faster testing, validation, and seamless deployment cycles.
- Enhanced Stability: Isolation of microservices improved system stability, mitigating the impact of issues in one service on others.
- Security Fortification: Precise security configurations at the microservice level bolstered data protection and compliance.
- Improved Profitability: Reduced downtime, improved user experience, and faster feature rollouts contributed to increased profitability.
- Cost Optimization: AWS ECS allowed for resource auto-scaling, ensuring cost-efficiency by only utilizing the necessary resources.
- Streamlined Monitoring and Management: With the application’s move to ECS, we have enhanced monitoring and management capabilities. This allows to proactively identify and address issues, ensuring smooth operations and customer satisfaction.
- Enhanced Security: Moving application to a private network has significantly improved security posture. It reduces exposure to external threats and vulnerabilities, making it more challenging for unauthorized parties to access systems. Data privacy and security have been enhanced, safeguarding sensitive information, and reducing the risk of breaches.
- Improved Compliance: Hosting the application in a private network has made it easier to meet regulatory and compliance requirements. With better control over who can access systems, we’ve taken strides in ensuring our application adheres to necessary security and compliance standards.
Security Considerations
- Utilized AWS IAM roles to restrict users to only the necessary resources, ensuring principle of least privilege and enhancing security across the ECS workload.
- Maintained comprehensive visibility into API calls through AWS CloudTrail, capturing detailed logs of user activities including who performed actions, what actions were taken, and from where they were initiated. This tracking ensures accountability and aids in compliance and auditing.
- For any administrative tasks, remote users were required to connect through a VPN client to access the ECS services. SSH access was tightly controlled, bound to a secure VPN server, and default ports were changed to custom ports for added security.
- The RDS database ports were made accessible only from the ECS tasks and restricted using Security Groups to ensure that only authorized application containers could connect, mitigating potential security risks.
- Deployed all container workloads within private subnets, enhancing security by isolating them from the public internet. The application was exposed using an Application Load Balancer (ALB) configured with SSL listeners, providing secure SSL certificates were issued through AWS Certificate Manager (ACM) to ensure encrypted communication.
AWS Services used:
AWS ECS, EC2, ALB, S3, CloudFormation, Autoscaling, CloudWatch, RDS, Lambda, CloudTrail, EC2 Lifecycle Management, VPC Endpoint, CloudWatch Logs, AWS Config, Security Hub, AWS SNS, Code Pipeline, Code Deploy, Code Build
Managed Services Delivered by Workmates
- Patch Management: Automated monthly patching using SSM Patch Manager for OS and application components.
- Monitoring & Alerting: 24×7 observability using CloudWatch, CloudTrail, and Guard
Duty. Alerts routed via SNS to engineering teams. - Compliance & Audit Readiness: Enabled drift detection via AWS Config and mapped access logs for SOC/ISO readiness.
- Performance Optimization: Periodic cost reviews and performance tuning across
compute, storage, and databases. - Capacity & Cost Management: Tagged resources for chargeback; utilized AWS Trusted Advisor and Savings Plans for cost reduction.
- Incident Management & SLA Monitoring: Integrated into ITSM system to track alerts and resolution SLAs.
CICD Architecture and Flow
Solution Architecture