Cloud Security Posture Management (CSPM) is a crucial aspect of ensuring the security of cloud computing environments. As more businesses migrate their applications and data to the cloud, it becomes crucial to maintain a strong security posture to protect sensitive information and maintain regulatory compliance. Here are some key reasons highlighting the importance of Cloud Security Posture Management:
- Visibility and Control:CSPM provides visibility into an organization’s cloud infrastructure, including resources, configurations, and potential vulnerabilities. This visibility is essential for maintaining control over the security posture of cloud assets.
- Configuration Management:
Cloud environments are dynamic, and misconfigurations are a common cause of security breaches. CSPM tools help organizations enforce security best practices by identifying and remediating misconfigurations in real-time. This reduces the attack surface and minimizes the risk of security incidents. - Compliance Assurance:
Many industries and regions have specific regulatory requirements for data protection and privacy. CSPM tools assist in ensuring compliance with these regulations by continuously monitoring configurations and settings to meet the necessary standards. - Threat Detection and Response:
CSPM solutions can detect and alert on potential security threats and vulnerabilities in real-time. This proactive approach allows organizations to respond quickly to security incidents, reducing the likelihood of data breaches or unauthorized access. - Automation and Orchestration:
Automation is a key component of CSPM, enabling organizations to automate the identification and remediation of security issues. This helps in maintaining a consistent and secure cloud environment, especially in large-scale and rapidly changing infrastructures. - Risk Management:
CSPM tools provide risk assessment and management capabilities, allowing organizations to prioritize and address the most critical security issues. This risk-based approach helps in allocating resources effectively and focusing on mitigating the most impactful threats. - Multi-Cloud Security:
Organizations often use multiple cloud service providers or have a hybrid cloud architecture. CSPM solutions provide a unified approach to security management across different cloud platforms, ensuring a consistent level of security regardless of the cloud provider. - Continuous Monitoring and Compliance:
CSPM involves continuous monitoring of the cloud environment, which is crucial for identifying and addressing security issues as they arise. Regular checks against security policies and compliance standards help maintain a secure posture over time. - Cost Efficiency:
By preventing security incidents through proactive measures, CSPM contributes to cost savings. The financial impact of a security breach, including potential data loss, downtime, and reputational damage, can be substantial. Investing in CSPM is a proactive measure to avoid such costs. - Policy Enforcement:
-
- Define and enforce security policies to govern the use of cloud resources.
- Implement access controls and permissions based on the principle of least privilege.
- Regularly review and update security policies to adapt to evolving threats and compliance requirements.
There are various tools available to help organizations manage and enhance their cloud security posture. These tools cover a range of security aspects, including risk assessment, configuration management, monitoring, and compliance. Here are some popular cloud security management tools:
- AWS Security Hub
- A comprehensive security service that provides centralized security management and compliance checks across an AWS environment.
- Aggregates, organizes, and prioritizes security findings from various AWS services.
- Azure Security Center:
- Microsoft Azure’s integrated security management system that provides threat protection across all Azure workloads.
- Offers advanced threat detection across hybrid cloud workloads, security policy management, and security posture management.
- Google Cloud Security Command Center (SCC):
-
- Provides a centralized view of the security status of Google Cloud resources.
- Helps organizations understand, prevent, and respond to threats in their Google Cloud environment.
- ScoutSuite:
-
- Open-source multi-cloud security auditing tool that supports AWS, Azure, and GCP.
- Assesses security posture by analyzing configurations, permissions, and identifying potential vulnerabilities.
- Dome9 (by Check Point):
-
- Offers security and compliance automation for public cloud environments, including AWS, Azure, and Google Cloud Platform.
- Provides visualization of network traffic, continuous compliance monitoring, and security posture management.
- Prowler
Prowler is an Open Source security tool to perform AWS, GCP and Azure security best practices assessments, audits. Offers incident response, continuous monitoring, hardening and forensics readiness. - Qualys Cloud Security:
-
- Provides a cloud-native security solution for continuous security and compliance monitoring.
- Offers vulnerability management, policy compliance, and threat protection for cloud environments.
When selecting a cloud security management tool, it’s important for organizations to consider their specific requirements, the cloud service providers they use, and the overall architecture of their cloud infrastructure. Additionally, integration with existing security workflows and the ability to automate security policies are key factors to consider.
In this blog, we will select and compare 3 of the popular CSPM tools for AWS cloud – namely AWS Security hub, Prowler & TrendMicro Conformity.
AWS Security Hub:
- Overview:
-
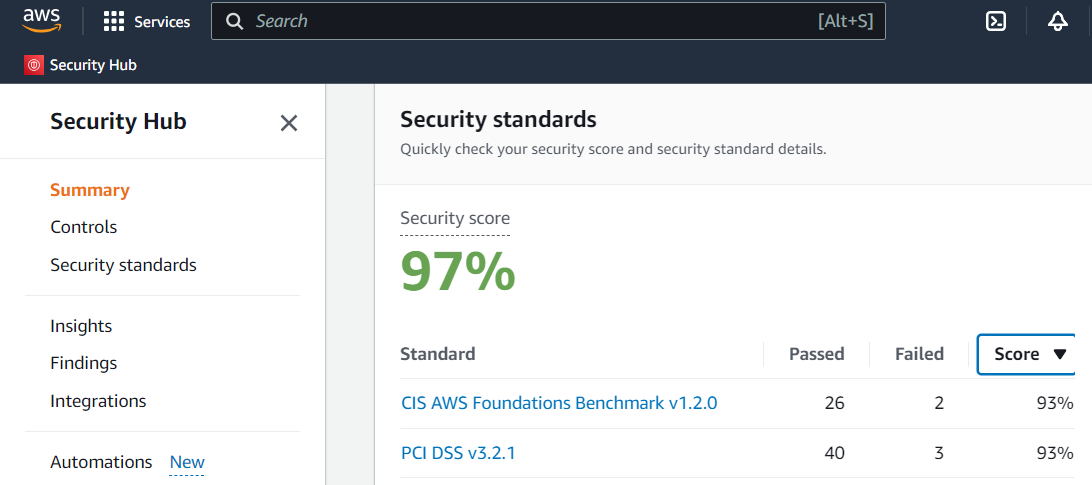
- AWS Security Hub is a centralized security service provided by Amazon Web Services.
- It aggregates and prioritizes security findings from various AWS services, third-party products, and AWS Partner Network (APN) security solutions.
- Key Features:
-
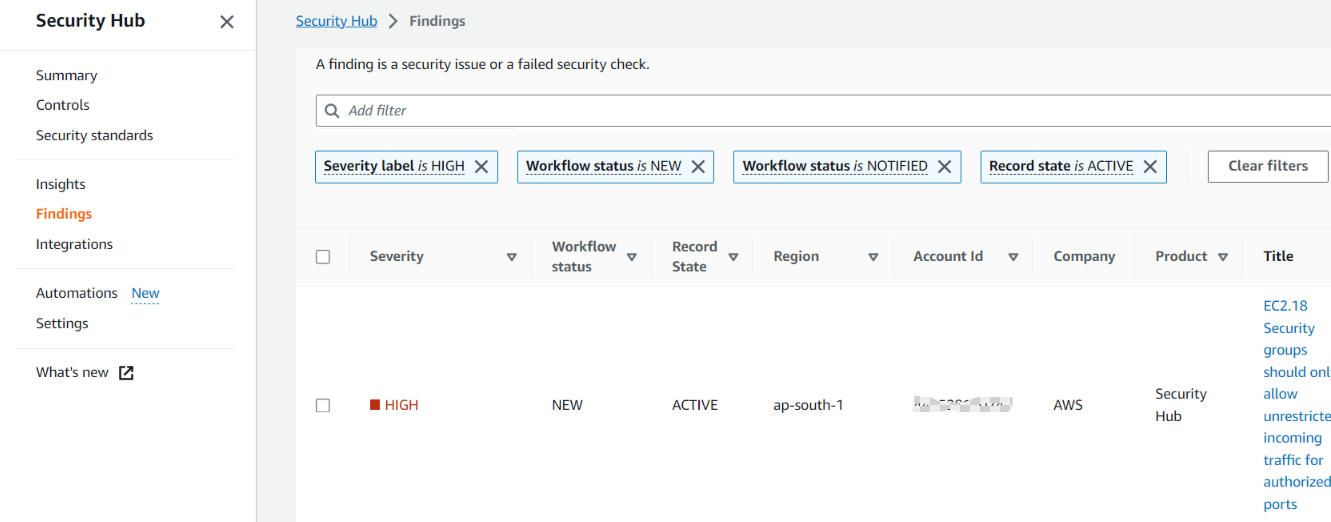
- Aggregates and normalizes findings from AWS services like Amazon GuardDuty, AWS Inspector, and Amazon Macie.
- Provides a comprehensive view of the security state of an AWS environment.
- Enables automated compliance checks against industry standards and best practices.
- Offers integration with other AWS services for automated response and remediation.
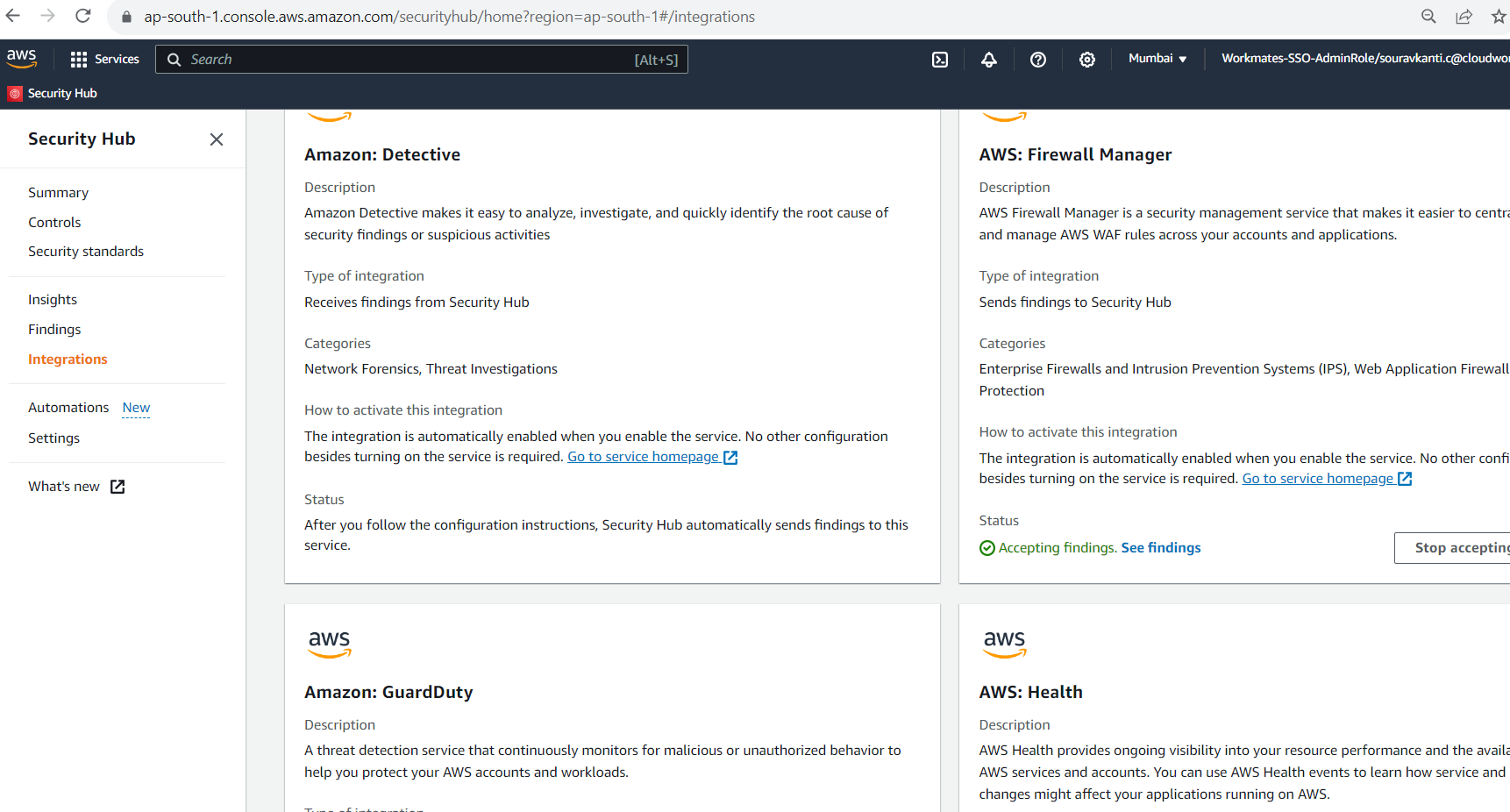
 Multiple integration option available
Multiple integration option available
Prowler:
Overview:
-
- Prowler is an open-source security tool specifically designed for AWS environments.
- It focuses on security best practices and provides a set of checks based on industry standards and security recommendations.
Key features of Prowler include:
- Security Best Practices Checks:
-
- Prowler includes checks for AWS security best practices, covering areas such as identity and access management, networking, logging, encryption, and more.
- Automated Scanning:
-
- The tool is designed to be automated and can be integrated into continuous integration/continuous deployment (CI/CD) pipelines or scheduled for regular scans.
- Support for Multiple AWS Accounts:
-
- Prowler can be configured to scan multiple AWS accounts, making it suitable for organizations with complex AWS environments.
- Output in Various Formats:
-
- Prowler generates reports in various formats, including plain text, JSON, and Markdown, making it flexible for different use cases and reporting needs.
- Container Support:
-
- Prowler can be run within a Docker container, making it easy to deploy and use in different environments.
Here’s a basic overview of how to use Prowler:
- Clone the Prowler repository from GitHub: git clone https://github.com/toniblyx/prowler
- Run Prowler: ./prowler
- Review the generated report for any identified issues or misconfigurations.
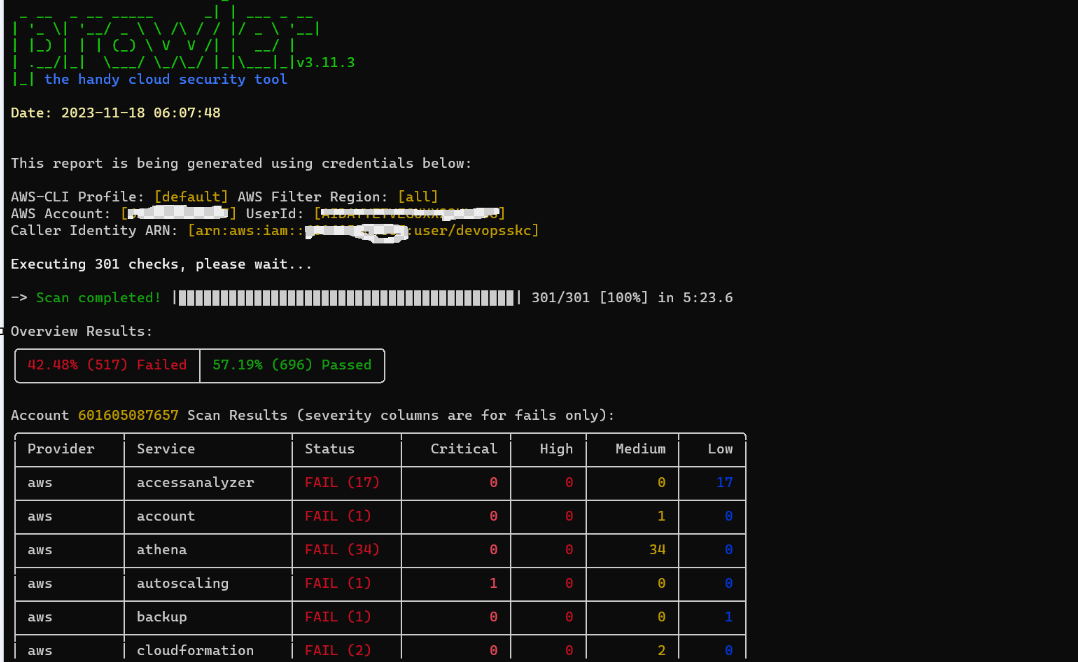
Prowler provide output/result in different format including csv and html
The report in html format has very nice visual with remediation/recommendation against the compliance fail check
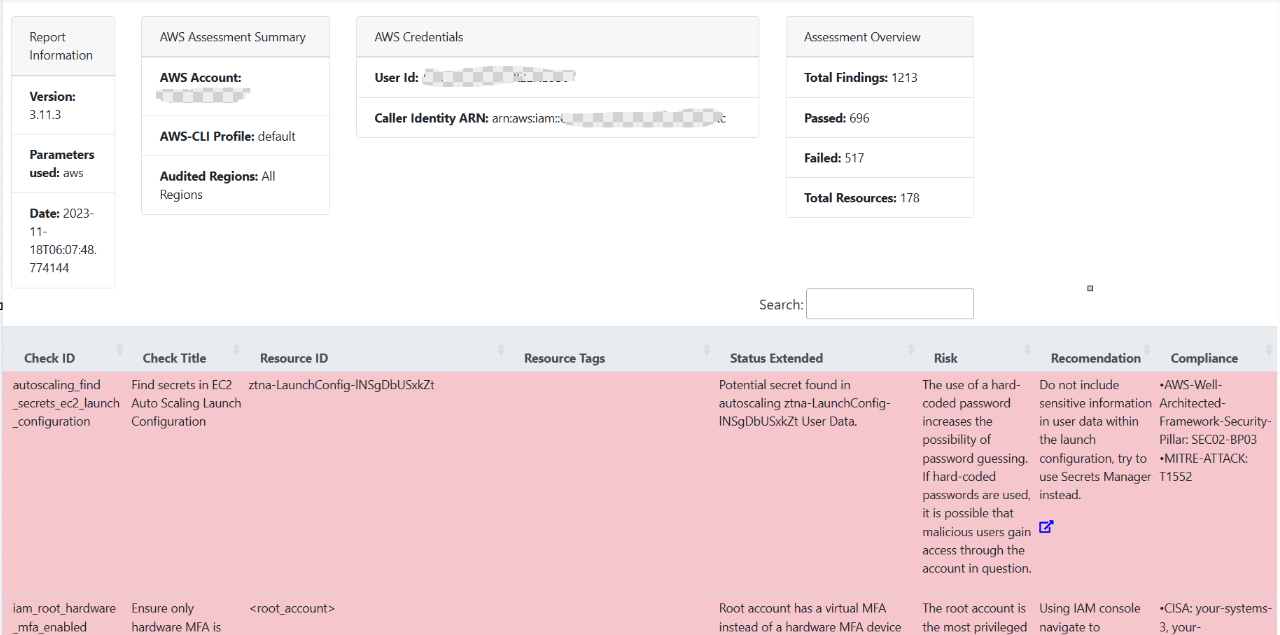
It’s important to note that while Prowler provides valuable insights into AWS security best practices, it is just one part of an overall cloud security strategy. Organizations should complement tools like Prowler with other cloud security management tools (e.g AWS Securityhub), practices, and policies to ensure a robust and comprehensive security posture in the cloud. Regularly updating Prowler and staying informed about AWS best practices is crucial to maintaining an effective security posture.
Trend Micro Conformity is a cloud security and compliance posture management tool designed to help organizations ensure the security and compliance of their cloud infrastructure, particularly in Amazon Web Services (AWS) environments.
Key features of Trend Micro Conformity include:
- Continuous Monitoring:
-
- Provides continuous monitoring of AWS configurations to identify and alert on potential security risks and compliance violations.
- Best Practice Checks:
-
- Conducts best practice checks based on AWS Well-Architected Framework and other industry standards to ensure adherence to security and operational best practices.
- Automated Remediation:
-
- Offers automated remediation capabilities to address identified misconfigurations and security issues, reducing the manual effort required for correction.
- Custom Policies:
-
- Allows organizations to define and enforce custom security policies tailored to their specific requirements and compliance standards.
- Integration with CI/CD Pipelines:
-
- Integrates with CI/CD pipelines to incorporate security checks into the development and deployment process.
- Risk Assessment:
-
- Performs risk assessments to identify and prioritize potential security risks, helping organizations focus on the most critical issues.
- Compliance Reporting:
-
- Generates compliance reports to assist with audits and regulatory requirements, providing evidence of adherence to security standards.
- Security Baseline Management:
-
- Assists in establishing and maintaining a secure baseline configuration for AWS resources.
- Multi-Account Support:
-
- Supports organizations with multiple AWS accounts, providing visibility and management across various environments.
- Alerting and Notifications:
-
- Sends alerts and notifications for security incidents or policy violations, enabling quick response to potential threats.
-
- seen as a proactive measure to prevent potential security incidents that could result in higher costs.
Conformity checks for 6 pillars of AWS well architect framework as other standards and frameworks like GDPR,CIS,HIPPA,NIST,PCI DSS etc
https://cloudone.trendmicro.com/docs/conformity/compliance-and-conformity/
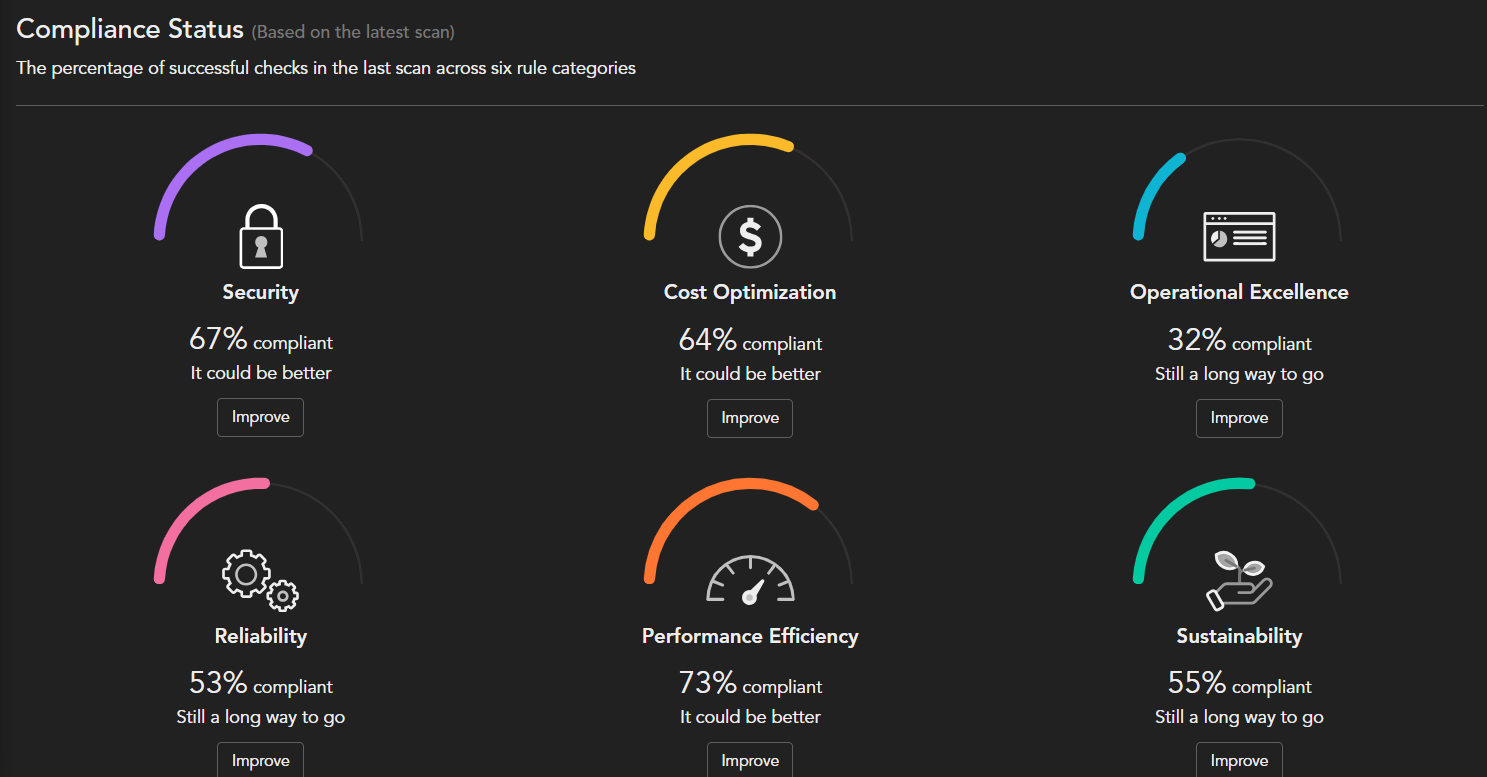
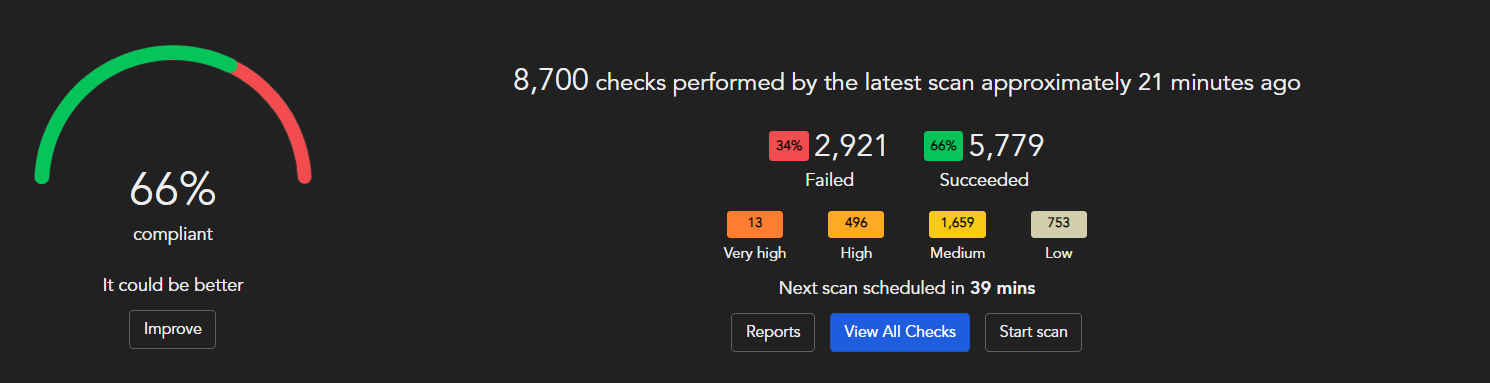
It provides report in both csv and html format
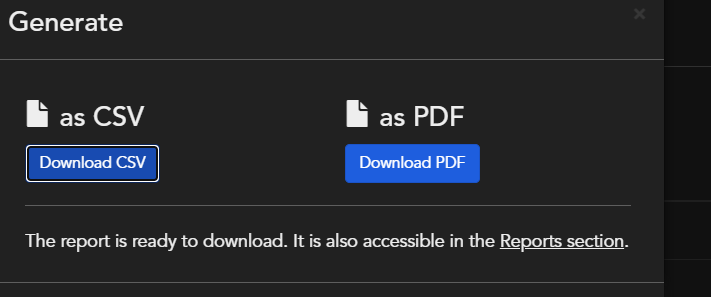
While Pdf reports looks better for review but csv records provide remediation/resolution link
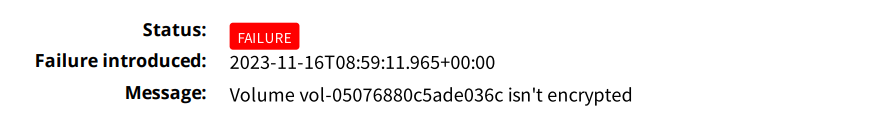
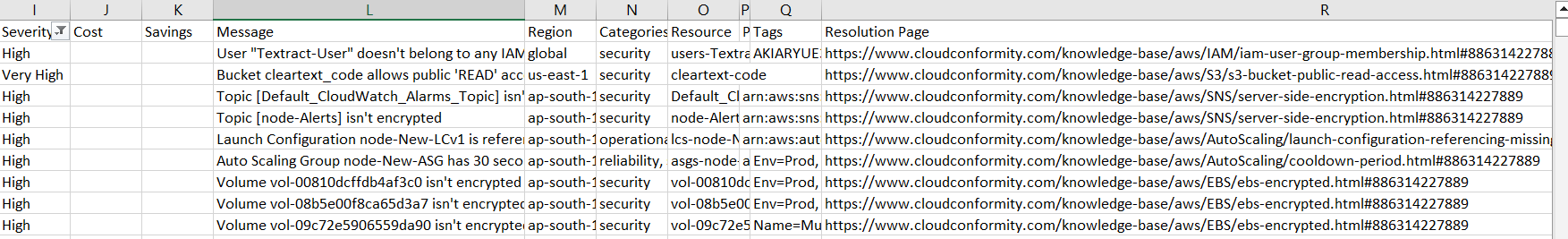
AWS Security Hub, Prowler, and Trend Micro Conformity are all tools designed to help organizations manage and enhance the security posture of their AWS environments. However, they serve different purposes and have distinct features. Let’s compare these tools:
Comparison:
- Scope:
-
- AWS Security Hub: Provides a holistic view of security findings from various AWS services.
- Prowler: Concentrates on automated security best practices checks specifically for AWS.
- Trend Micro Conformity: Focuses on AWS environments, offering continuous monitoring and automated remediation.
- Automation:
-
- AWS Security Hub: Provides integration with AWS Lambda for automated response.
- Prowler: Offers automation for continuous security checks, but remediation may need additional tools or scripts.
- Trend Micro Conformity: Emphasizes automated remediation for identified misconfigurations.
- Customization:
-
- AWS Security Hub: Offers some customization, especially regarding compliance standards.
- Prowler: Provides flexibility through customizable checks.
- Trend Micro Conformity: Allows customization of policies to align with specific security requirements.
- Ease of Use:
-
- AWS Security Hub: Integrated into the AWS Management Console for ease of use.
- Prowler: Command-line tool, requires some technical expertise.
- Trend Micro Conformity: Web-based interface with user-friendly features.
- Deployment:
-
- AWS Security Hub: Managed AWS service.
- Prowler: Open-source tool to be deployed and run by users.
- Trend Micro Conformity: Cloud-based service.
The choice between AWS Security Hub, Prowler, and Trend Micro Conformity depends on specific organizational requirements, preferences, and the level of automation and customization needed. Some organizations may choose to use a combination of these tools to achieve a comprehensive approach to AWS security posture management.
Each Cloud Security Posture Management (CSPM) tool, including Trend Micro Conformity, has its own set of features and advantages. It’s important to note that the landscape of cloud security tools may evolve, and newer updates or releases may impact the features and capabilities of these tools. As of now, here are some potential advantages of Trend Micro Conformity over other CSPM tools:
- Automated Remediation:
-
- Trend Micro Conformity emphasizes automated remediation of identified misconfigurations. This can be a significant advantage, as it streamlines the process of fixing security issues, reducing manual effort and response time.
- Focused on AWS:
-
- Trend Micro Conformity is specifically designed for AWS environments. If your organization primarily operates on AWS and requires a tool tailored to AWS security best practices, Trend Micro Conformity’s focused approach might be advantageous.
- Customizable Policies:
-
- The ability to customize policies is crucial for aligning security practices with organizational requirements. Trend Micro Conformity allows users to customize policies to meet specific security and compliance needs.
- User-Friendly Interface:
-
- Trend Micro Conformity provides a web-based interface that is designed to be user-friendly. This can be advantageous for organizations that prefer tools with intuitive interfaces, making it easier for security teams to navigate and use effectively.
- Integration with CI/CD Pipelines:
-
- Integration with CI/CD pipelines is essential for organizations that follow DevOps practices. Trend Micro Conformity offers integration capabilities, allowing security checks to be incorporated into the development and deployment processes.
- Continuous Monitoring:
-
- Continuous monitoring of AWS configurations is a key feature of Trend Micro Conformity. This provides real-time visibility into the security posture of your AWS environment, helping organizations stay proactive in addressing security issues.
- Global Best Practices:
-
- Trend Micro Conformity aligns its checks with global best practices. This can be advantageous for organizations that prioritize adherence to widely recognized security standards and frameworks.
- Vendor Expertise:
-
- Trend Micro is a well-established cybersecurity vendor with a history of providing security solutions. Organizations may consider this factor when choosing a CSPM tool, as it can provide a level of confidence in the tool’s effectiveness and support.
When evaluating CSPM tools, it’s crucial to consider the specific needs and context of your organization. Factors such as the complexity of your cloud environment, compliance requirements, integration capabilities, and the level of automation required should all be taken into account. Additionally, it’s advisable to conduct a trial or proof of concept to assess how well a tool aligns with your organization’s unique use cases and requirements.
In summary, Cloud Security Posture Management is essential for organizations to maintain a secure, compliant, and well-managed cloud environment. It helps mitigate risks, detect and respond to threats, and ensures that cloud configurations align with security best practices and industry regulations.
As organizations increasingly adopt cloud services to store, process, and manage their data, the need for effective security measures becomes paramount
Ultimately, the decision to buy or implement cloud posture security management tools should align with your organization’s overall security strategy, risk tolerance, and long-term goals. Regular assessments of your cloud environment, coupled with a thorough understanding of compliance requirements and security best practices, will guide the timing of such investments




